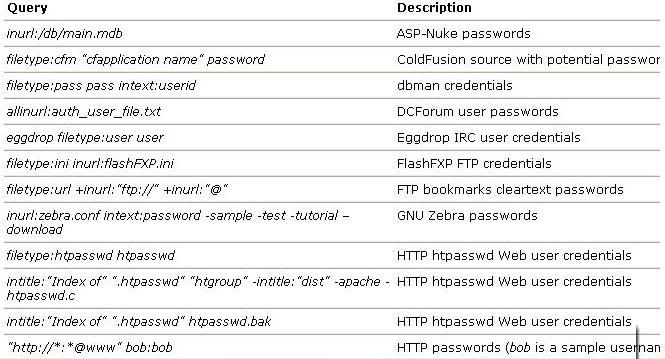
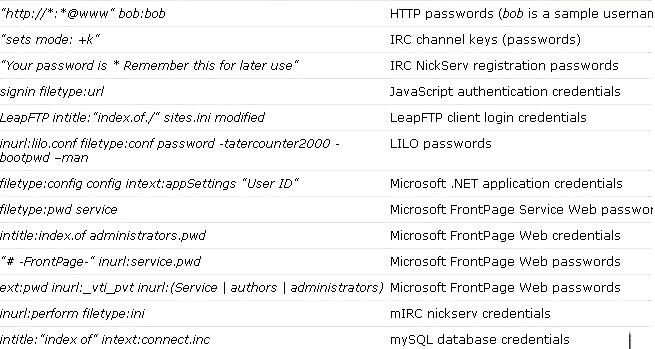
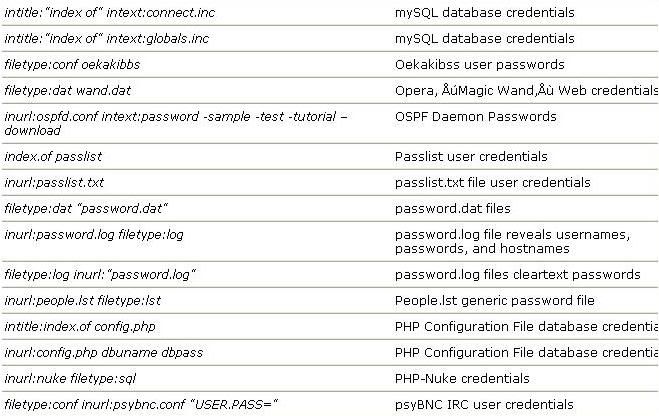
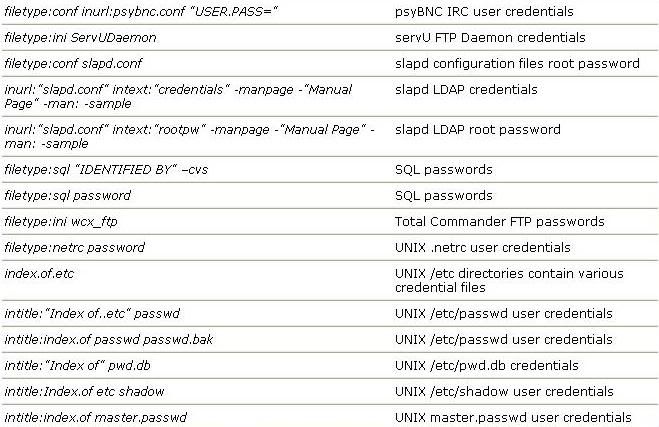
Here Is queries which can be used in day to day life & for noobs.. 
Below discussed are various Google’s special commands and I shall be explaining each command in
brief and will show how it can be used for critical information digging.
[ intitle: ]
The “intitle:” syntax helps Google restrict the search results to pages containing that word in the title. For
example, “intitle: login password” (without quotes) will return links to those pages that has the word
"login" in their title, and the word "password" anywhere in the page.
Similarly, if one has to query for more than one word in the page title then in that case “allintitle:” can be
used instead of “intitle” to get the list of pages containing all those words in its title. For example using
“intitle: login intitle: password” is same as querying “allintitle: login password”.
[ inurl: ]
The “inurl:” syntax restricts the search results to those URLs containing the search keyword. For
example: “inurl: passwd” (without quotes) will return only links to those pages that have "passwd" in the
URL.
Similarly, if one has to query for more than one word in an URL then in that case “allinurl:” can be used
instead of “inurl” to get the list of URLs containing all those search keywords in it. For example: “allinurl:
etc/passwd“ will look for the URLs containing “etc” and “passwd”. The slash (“/”) between the words will
be ignored by Google.
[ site: ]
The “site:” syntax restricts Google to query for certain keywords in a particular site or domain. For
example: “exploits site:hackingspirits.com” (without quotes) will look for the keyword “exploits” in those
pages present in all the links of the domain “hackingspirits.com”. There should not be any space between
“site:” and the “domain name”.
[ filetype: ]
This “filetype:” syntax restricts Google search for files on internet with particular extensions (i.e. doc, pdf
or ppt etc). For example: “filetype:doc site:gov confidential” (without quotes) will look for files with “.doc”
extension in all government domains with “.gov” extension and containing the word “confidential” either in
the pages or in the “.doc” file. i.e. the result will contain the links to all confidential word document files on
the government sites.
[ link: ]
“link:” syntax will list down webpages that have links to the specified webpage. For Example:
“link:www.securityfocus.com” will list webpages that have links pointing to the SecurityFocus homepage.
Note there can be no space between the "link:" and the web page url.
Demystifying Google Hacks
By Debasis Mohanty
[ related: ]
The “related:” will list web pages that are "similar" to a specified web page. For Example:
“related:www.securityfocus.com” will list web pages that are similar to the Securityfocus homepage. Note
there can be no space between the "related:" and the web page url.
[ cache: ]
The query “cache:” will show the version of the web page that Google has in its cache. For Example:
“cache:www.hackingspirits.com” will show Google' cache of the Google homepage. Note there can be
s
no space between the "cache:" and the web page url.
If you include other words in the query, Google will highlight those words within the cached document. For
Example: “cache:www.hackingspirits.com guest” will show the cached content with the word "guest"
highlighted.
[ intext: ]
The “intext:” syntax searches for words in a particular website. It ignores links or URLs and page titles.
For example: “intext:exploits” (without quotes) will return only links to those web pages that has the
search keyword "exploits" in its webpage.
[ phonebook: ]
“phonebook” searches for U.S. street address and phone number information. For Example:
“phonebook:Lisa+CA” will list down all names of person having “Lisa” in their names and located in
“California (CA)”. This can be used as a great tool for hackers incase someone want to do dig personal information for social engineering.
Google serves almost 80 % all search queries on the Internet, proving itself as the most popular search engine. However Google makes it possible to reach not only the publicly available information resources, but also gives access to some of the most confidential information that should never have been revealed. In this post I will show how to use Google for exploiting security vulnerabilities within websites.The following are some of the hacks that can be accomplished using Google.
1. Hacking Security Cameras
There exists many security cameras used for monitoring places like parking lots, college campus, road traffic etc. which can be hacked using Google so that you can view the images captured by those cameras in real time. All you have to do is use the following search query in Google. Type in Google search box exactly as follows and hit enter inurl:”viewerframe?mode=motion” Click on any of the search results (Top 5 recommended) and you will gain access to the live camera which has full controls. You will see something as follows
As you can see in the above screenshot, you now have access to the Live cameras which work in real-time. You can also move the cameras in all the four directions, perform actions such as zoom in and zoom out. This camera has really a less refresh rate. But there are other search queries through you can gain access to other cameras which have faster refresh rates. So to access them just use the following search query.
intitle:”Live View / – AXIS”
Click on any of the search results to access a different set of live cameras. Thus you have hacked Security Cameras using Google.
2. Hacking Personal and Confidential Documents
Using Google it is possible to gain access to an email repository containing CV of hundreds of people which were created when applying for their jobs. The documents containing their Address, Phone, DOB, Education, Work experience etc. can be found just in seconds.
intitle:”curriculum vitae” “phone * * *” “address *” “e-mail”
You can gain access to a list of .xls (excel documents) which contain contact details including email addresses of large group of people. To do so, type the following search query and hit enter.
filetype:xls inurl:”email.xls”
Also it’s possible togain access to documents potentially containing information on bank accounts, financial summaries and credit card numbers using the following search query
intitle:index.of finances.xls
3. Hacking Google to gain access to Free Stuffs
Ever wondered how to hack Google for free music or ebooks. Well here is a way to do that. To download free music just enter the following query on google search box and hit enter.
“?intitle:index.of?mp3eminem“
Now you’ll gain access to the whole index of eminem album where in you can download the songs of your choice. Instead of eminem you can subtitute the name of your favorite album. To search for the ebooks all you have to do is replace “eminem” with your favorite book name. Also replace “mp3″ with “pdf” or “zip” or “rar”.
------------------------------------------
Now this what i call Hardcore:
****USE AT UR RISK N DON'T ASK HW TO USE IT***
*** NOW THIS IS PURE 18+ STUFF ***
Querying for vulnerable sites or servers using Google’s advance syntaxes
Well, the Google’s query syntaxes discussed above can really
help people to precise their search and get what they are
exactly looking for.
Now Google being so intelligent search engine, malicious users
don’t mind exploiting its ability to dig confidential and secret
information from internet which has got restricted access. Now I
shall discuss those techniques in details how malicious user dig
information from internet using Google as a tool.
Using “Index of ” syntax to find sites enabled with Index browsing
A webserver with Index browsing enabled means anyone can browse
the webserver directories like ordinary local directories. Here
I shall discuss how one can use “index of” syntax to get a list
links to webserver which has got directory browsing enabled.
This becomes an easy source for information gathering for a
hacker. Imagine if the get hold of password files or others
sensitive files which are not normally visible to the internet.
Below given are few examples using which one can get access to
many sensitive information much easily.
Index of /admin
Index of /passwd
Index of /password
Index of /mail
"Index of /" +passwd
"Index of /" +password.txt
"Index of /" +.htaccess
"Index of /secret"
"Index of /confidential"
"Index of /root"
"Index of /cgi-bin"
"Index of /credit-card"
"Index of /logs"
"Index of /config"
Looking for vulnerable sites or servers using [/s3]“inurl:” or “allinurl:”[/s3]
a. Using “allinurl: winnt/system32/ ” (without quotes) will list
down all the links to the server which gives access to
restricted directories like “system32” through web. If you are
lucky enough then you might get access to the cmd.exe in the
“system32” directory. Once you have the access to “cmd.exe”
and are able to execute it then you can go ahead in further
escalating your privileges over the server and compromise it.
b. Using “allinurl: wwwboard/passwd.txt ” (without quotes) in the
Google search will list down all the links to the server which
are vulnerable to “WWWBoard Password vulnerability”. For more info Google it out.
c. Using “inurl: .bash_history ” (without quotes) will list down
all the links to the server which gives access to
“.bash_history” file through web. This is a command history
file. This file includes the list of command executed by the
administrator, and sometimes includes sensitive information
such as password typed in by the administrator. If this file
is compromised and if contains the encrypted unix (or *nix)
password then it can be easily cracked using “John The
Ripper”.
d. Using “ inurl: config.txt” (without quotes) will list down all
the links to the servers which gives access to “config.txt”
file through web. This file contains sensitive information,
including the hash value of the administrative password and
database authentication credentials. For Example: Ingenium
Learning Management System is a Web-based application for
Windows based systems developed by Click2learn, Inc. Ingenium
Learning Management System versions 5.1 and 6.1 stores
sensitive information insecurely in the config.txt file.
Other similar search using “inurl:” or “allinurl:” combined with other syntaxs
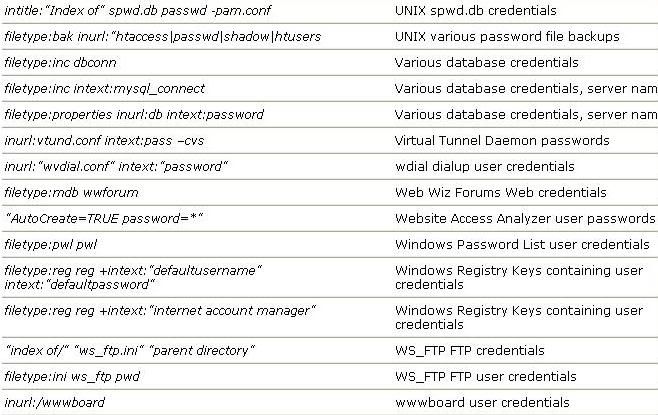
inurl:admin filetype:txt
inurl:admin filetype:db
inurl:admin filetype:cfg
inurl:mysql filetype:cfg
inurl:passwd filetype:txt
inurl:iisadmin
inurl:auth_user_file.txt
inurl: orders.txt
inurl:"wwwroot/*."
inurl:adpassword.txt
inurl:webeditor.php
inurl:file_upload.php
inurl:gov filetype:xls "restricted"
index of ftp +.mdb allinurl:/cgi-bin/ +mailto
Looking for vulnerable sites or servers using “intitle:” or “allintitle:”
a. Using [ allintitle: "index of /root”] (without brackets) will
list down the links to the web server which gives access to
restricted directories like “root” through web. This directory
sometimes contains sensitive information which can be easily
retrieved through simple web requests.
b. Using [ allintitle: "index of /admin”] (without brackets) will
list down the links to the websites which has got index
browsing enabled for restricted directories like “admin”
through web. Most of the web application sometimes uses names
like “admin” to store admin credentials in it. This directory
sometimes contains sensitive information which can be easily
retrieved through simple web requests.
Other similar search using “intitle:” or “allintitle:” combined with other syntaxs
intitle:"Index of" .sh_history
intitle:"Index of" .bash_history
intitle:"index of" passwd
intitle:"index of" people.lst
intitle:"index of" pwd.db
intitle:"index of" etc/shadow
intitle:"index of" spwd
intitle:"index of" master.passwd
intitle:"index of" htpasswd
intitle:"index of" members OR accounts
intitle:"index of" user_carts OR user_cart
allintitle: sensitive filetype:doc
allintitle: restricted filetype :mail
allintitle: restricted filetype:doc site:gov
Other interesting Search Queries
To search for sites vulnerable to Cross-Sites Scripting (XSS) attacks:
allinurl:/scripts/cart32.exe
allinurl:/CuteNews/show_archives.php
allinurl:/phpinfo.php
To search for sites vulnerable to SQL Injection attacks:
allinurl:/privmsg.php
allinurl:/privmsg.php

Below discussed are various Google’s special commands and I shall be explaining each command in
brief and will show how it can be used for critical information digging.
[ intitle: ]
The “intitle:” syntax helps Google restrict the search results to pages containing that word in the title. For
example, “intitle: login password” (without quotes) will return links to those pages that has the word
"login" in their title, and the word "password" anywhere in the page.
Similarly, if one has to query for more than one word in the page title then in that case “allintitle:” can be
used instead of “intitle” to get the list of pages containing all those words in its title. For example using
“intitle: login intitle: password” is same as querying “allintitle: login password”.
[ inurl: ]
The “inurl:” syntax restricts the search results to those URLs containing the search keyword. For
example: “inurl: passwd” (without quotes) will return only links to those pages that have "passwd" in the
URL.
Similarly, if one has to query for more than one word in an URL then in that case “allinurl:” can be used
instead of “inurl” to get the list of URLs containing all those search keywords in it. For example: “allinurl:
etc/passwd“ will look for the URLs containing “etc” and “passwd”. The slash (“/”) between the words will
be ignored by Google.
[ site: ]
The “site:” syntax restricts Google to query for certain keywords in a particular site or domain. For
example: “exploits site:hackingspirits.com” (without quotes) will look for the keyword “exploits” in those
pages present in all the links of the domain “hackingspirits.com”. There should not be any space between
“site:” and the “domain name”.
[ filetype: ]
This “filetype:” syntax restricts Google search for files on internet with particular extensions (i.e. doc, pdf
or ppt etc). For example: “filetype:doc site:gov confidential” (without quotes) will look for files with “.doc”
extension in all government domains with “.gov” extension and containing the word “confidential” either in
the pages or in the “.doc” file. i.e. the result will contain the links to all confidential word document files on
the government sites.
[ link: ]
“link:” syntax will list down webpages that have links to the specified webpage. For Example:
“link:www.securityfocus.com” will list webpages that have links pointing to the SecurityFocus homepage.
Note there can be no space between the "link:" and the web page url.
Demystifying Google Hacks
By Debasis Mohanty
[ related: ]
The “related:” will list web pages that are "similar" to a specified web page. For Example:
“related:www.securityfocus.com” will list web pages that are similar to the Securityfocus homepage. Note
there can be no space between the "related:" and the web page url.
[ cache: ]
The query “cache:” will show the version of the web page that Google has in its cache. For Example:
“cache:www.hackingspirits.com” will show Google' cache of the Google homepage. Note there can be
s
no space between the "cache:" and the web page url.
If you include other words in the query, Google will highlight those words within the cached document. For
Example: “cache:www.hackingspirits.com guest” will show the cached content with the word "guest"
highlighted.
[ intext: ]
The “intext:” syntax searches for words in a particular website. It ignores links or URLs and page titles.
For example: “intext:exploits” (without quotes) will return only links to those web pages that has the
search keyword "exploits" in its webpage.
[ phonebook: ]
“phonebook” searches for U.S. street address and phone number information. For Example:
“phonebook:Lisa+CA” will list down all names of person having “Lisa” in their names and located in
“California (CA)”. This can be used as a great tool for hackers incase someone want to do dig personal information for social engineering.
Google serves almost 80 % all search queries on the Internet, proving itself as the most popular search engine. However Google makes it possible to reach not only the publicly available information resources, but also gives access to some of the most confidential information that should never have been revealed. In this post I will show how to use Google for exploiting security vulnerabilities within websites.The following are some of the hacks that can be accomplished using Google.
1. Hacking Security Cameras
There exists many security cameras used for monitoring places like parking lots, college campus, road traffic etc. which can be hacked using Google so that you can view the images captured by those cameras in real time. All you have to do is use the following search query in Google. Type in Google search box exactly as follows and hit enter inurl:”viewerframe?mode=motion” Click on any of the search results (Top 5 recommended) and you will gain access to the live camera which has full controls. You will see something as follows
As you can see in the above screenshot, you now have access to the Live cameras which work in real-time. You can also move the cameras in all the four directions, perform actions such as zoom in and zoom out. This camera has really a less refresh rate. But there are other search queries through you can gain access to other cameras which have faster refresh rates. So to access them just use the following search query.
intitle:”Live View / – AXIS”
Click on any of the search results to access a different set of live cameras. Thus you have hacked Security Cameras using Google.
2. Hacking Personal and Confidential Documents
Using Google it is possible to gain access to an email repository containing CV of hundreds of people which were created when applying for their jobs. The documents containing their Address, Phone, DOB, Education, Work experience etc. can be found just in seconds.
intitle:”curriculum vitae” “phone * * *” “address *” “e-mail”
You can gain access to a list of .xls (excel documents) which contain contact details including email addresses of large group of people. To do so, type the following search query and hit enter.
filetype:xls inurl:”email.xls”
Also it’s possible togain access to documents potentially containing information on bank accounts, financial summaries and credit card numbers using the following search query
intitle:index.of finances.xls
3. Hacking Google to gain access to Free Stuffs
Ever wondered how to hack Google for free music or ebooks. Well here is a way to do that. To download free music just enter the following query on google search box and hit enter.
“?intitle:index.of?mp3eminem“
Now you’ll gain access to the whole index of eminem album where in you can download the songs of your choice. Instead of eminem you can subtitute the name of your favorite album. To search for the ebooks all you have to do is replace “eminem” with your favorite book name. Also replace “mp3″ with “pdf” or “zip” or “rar”.
------------------------------------------
Now this what i call Hardcore:
****USE AT UR RISK N DON'T ASK HW TO USE IT***






*** NOW THIS IS PURE 18+ STUFF ***
Querying for vulnerable sites or servers using Google’s advance syntaxes
Well, the Google’s query syntaxes discussed above can really
help people to precise their search and get what they are
exactly looking for.
Now Google being so intelligent search engine, malicious users
don’t mind exploiting its ability to dig confidential and secret
information from internet which has got restricted access. Now I
shall discuss those techniques in details how malicious user dig
information from internet using Google as a tool.
Using “Index of ” syntax to find sites enabled with Index browsing
A webserver with Index browsing enabled means anyone can browse
the webserver directories like ordinary local directories. Here
I shall discuss how one can use “index of” syntax to get a list
links to webserver which has got directory browsing enabled.
This becomes an easy source for information gathering for a
hacker. Imagine if the get hold of password files or others
sensitive files which are not normally visible to the internet.
Below given are few examples using which one can get access to
many sensitive information much easily.
Index of /admin
Index of /passwd
Index of /password
Index of /mail
"Index of /" +passwd
"Index of /" +password.txt
"Index of /" +.htaccess
"Index of /secret"
"Index of /confidential"
"Index of /root"
"Index of /cgi-bin"
"Index of /credit-card"
"Index of /logs"
"Index of /config"
Looking for vulnerable sites or servers using [/s3]“inurl:” or “allinurl:”[/s3]
a. Using “allinurl: winnt/system32/ ” (without quotes) will list
down all the links to the server which gives access to
restricted directories like “system32” through web. If you are
lucky enough then you might get access to the cmd.exe in the
“system32” directory. Once you have the access to “cmd.exe”
and are able to execute it then you can go ahead in further
escalating your privileges over the server and compromise it.
b. Using “allinurl: wwwboard/passwd.txt ” (without quotes) in the
Google search will list down all the links to the server which
are vulnerable to “WWWBoard Password vulnerability”. For more info Google it out.
c. Using “inurl: .bash_history ” (without quotes) will list down
all the links to the server which gives access to
“.bash_history” file through web. This is a command history
file. This file includes the list of command executed by the
administrator, and sometimes includes sensitive information
such as password typed in by the administrator. If this file
is compromised and if contains the encrypted unix (or *nix)
password then it can be easily cracked using “John The
Ripper”.
d. Using “ inurl: config.txt” (without quotes) will list down all
the links to the servers which gives access to “config.txt”
file through web. This file contains sensitive information,
including the hash value of the administrative password and
database authentication credentials. For Example: Ingenium
Learning Management System is a Web-based application for
Windows based systems developed by Click2learn, Inc. Ingenium
Learning Management System versions 5.1 and 6.1 stores
sensitive information insecurely in the config.txt file.
Other similar search using “inurl:” or “allinurl:” combined with other syntaxs
inurl:admin filetype:txt
inurl:admin filetype:db
inurl:admin filetype:cfg
inurl:mysql filetype:cfg
inurl:passwd filetype:txt
inurl:iisadmin
inurl:auth_user_file.txt
inurl: orders.txt
inurl:"wwwroot/*."
inurl:adpassword.txt
inurl:webeditor.php
inurl:file_upload.php
inurl:gov filetype:xls "restricted"
index of ftp +.mdb allinurl:/cgi-bin/ +mailto
Looking for vulnerable sites or servers using “intitle:” or “allintitle:”
a. Using [ allintitle: "index of /root”] (without brackets) will
list down the links to the web server which gives access to
restricted directories like “root” through web. This directory
sometimes contains sensitive information which can be easily
retrieved through simple web requests.
b. Using [ allintitle: "index of /admin”] (without brackets) will
list down the links to the websites which has got index
browsing enabled for restricted directories like “admin”
through web. Most of the web application sometimes uses names
like “admin” to store admin credentials in it. This directory
sometimes contains sensitive information which can be easily
retrieved through simple web requests.
Other similar search using “intitle:” or “allintitle:” combined with other syntaxs
intitle:"Index of" .sh_history
intitle:"Index of" .bash_history
intitle:"index of" passwd
intitle:"index of" people.lst
intitle:"index of" pwd.db
intitle:"index of" etc/shadow
intitle:"index of" spwd
intitle:"index of" master.passwd
intitle:"index of" htpasswd
intitle:"index of" members OR accounts
intitle:"index of" user_carts OR user_cart
allintitle: sensitive filetype:doc
allintitle: restricted filetype :mail
allintitle: restricted filetype:doc site:gov
Other interesting Search Queries
To search for sites vulnerable to Cross-Sites Scripting (XSS) attacks:
allinurl:/scripts/cart32.exe
allinurl:/CuteNews/show_archives.php
allinurl:/phpinfo.php
To search for sites vulnerable to SQL Injection attacks:
allinurl:/privmsg.php
allinurl:/privmsg.php
Thanks for sharing such a nice article. i love your writing. your idea is mind blowing that's why i would like to appreciate your work. Free online jobs
ReplyDeleteIt is very useful blog and very informative thank you for sharing us.
ReplyDeleteIntraday Jackpot Trading Call || Silver Jackpot Calls
Nice blog and very interesting thank you for sharing us.
ReplyDeleteIntraday Jackpot Call
Very informative article. Thanks for sharing.Take a look to
ReplyDeleteour blog: coupon
deals
ReplyDeleteyour blogs is awesome.
videocon sms pack Rs.18
300 Loc/STD SMS 14 Days.
It is an amazing post.Very useful to me.I liked it .Take a look to my blog cash against credit card at low interest.
ReplyDeleteAwesome Post! here I got some amazing stuffgold tips advisor
ReplyDeleteNice post of GOOGLE Search Strings.
ReplyDeletethanks,
MCX Tips Free Trial
This comment has been removed by the author.
ReplyDeleteSuch a great blog.
ReplyDeleteCommodity Tips Free Trial | Silver Updates
This manages the most appealing for a various trends in the right way to hire something.
ReplyDeleteNifty Trading Tips
MCX Market Tips
waoo nice post about GOOGLE Search Strings
ReplyDeleteThanks,
Gold Jackpot Call Specialist
Thanks for this amazing article. Loved your post. Waiting for your next article.
ReplyDeleteIntraday Tips.
Hi! This is kind of off topic but I need some guidance from an established blog. Is it very hard to set up your own blog? I’m not very
ReplyDeletetechnical but I can figure things out pretty fast. I’m thinking about making my own but I’m not sure where to start.
Do you have any ideas or suggestions? Thanks